Note:
Microsoft has decided to charge for this service (8$ for each GB) …
Microsoft has launched a new feature that allows administrators to import PST to Exchange online directly through the portal.
In this article I’ll guide you through the steps of uploading one PST file and import it to a user’s mailbox. Although the steps are identical to Microsoft’s TechNet article but it’s more detailed and with screenshots.
So to achieve this, you’ll have to first sign in to your Office 365 portal. Open Exchange admin center and follow the below steps:
- Granting Permission
Grant your self-importing PST permission to users by navigating to Exchange admin center -> Permissions> Double click on Compliance Management
Under Roles: click on + and add Mailbox Import Export role
Click on + Under Members and add your user account
![clip_image001[5]](http://lh3.googleusercontent.com/-HhfvunQdrxQ/VcPSlVLzuhI/AAAAAAAAQjM/o0wYnyxb2pg/clip_image001%25255B5%25255D_thumb.png?imgmax=800)
2. `Copy Secure URL and secure storage account key
To get the Azure secure storage account key and URL you will have to go back to the Office 365 portal and then click on Import tab on the left pane
Then click on the Key sign below
![clip_image002[4]](http://lh3.googleusercontent.com/-cbQSUQycpX8/VcPSm0x02-I/AAAAAAAAQjc/XDCnr-Jss-A/clip_image002%25255B4%25255D_thumb.png?imgmax=800)
When you click on it, you will be able to retrieve the key and the URL by clicking on Copy Key and URL .
![clip_image003[4]](http://lh3.googleusercontent.com/-CyUJCpHxGQM/VcPSor9DutI/AAAAAAAAQjs/4d6SEICexgA/clip_image003%25255B4%25255D_thumb.png?imgmax=800)
The secure storage account key is pretty long and you’ll have to notice that sometimes you might get confused and copy only the appearing portion of it in the field… if you do so and copied that in the Azcopy command or Azure storage explorer you might get an error …
Here’s my Secure Storage account key that I am using on a trial version of Office 365.
KA9Z00rEYa1JlqGE4wO222MnsN5ywT0elOgLeNht/fSMIJPe2134hEChuuDJ5mfdknq8ts0+cez6uUvFzcQd6g==
Next: Copying the URL.
The URL has an important part which you will be using in Azure Storage Explorer tool in order to login and browse your Tenant’s storage which you’ll use to upload PST to.
The URL will appear as following.. You will need to copy the part in bold
https://d49d7ae0e38a4d8e9c93565.blob.core.windows.net/ingestiondata/
You have to copy this in to the storage account name
d49d7ae0e38a4d8e9c93565
3. Copying PST files to Azure Folder using Azcopy command or Azure Storage Explorer (You can use Azure Storage Explorer too)
In order to upload PST files to Azure, you have two methods. The first is using Azcopy command which is pretty easy and straightforward (but still CMD dependent) or you can use the GUI Application which is Azure Storage explorer
To download azcopy, you can use the following link
http://az635501.vo.msecnd.net/azcopy-3-2-0/MicrosoftAzureStorageTools.msi
Or download them from the Import page as well under Resources:
![clip_image004[4]](http://lh3.googleusercontent.com/-9krqrQn21RE/VcPSqQGfvnI/AAAAAAAAQj8/rAzWlys5s0k/clip_image004%25255B4%25255D_thumb.png?imgmax=800)
Once the tool is installed. Right click on it and open it as administrator
The following command will take all the files inside my local folder path C:\Users\Mohammed\Desktop\upload
It will create a folder in Azure’s default folder ingestiondata called “Server01/PSTshareR1/”
It will use the destkey that I have retrieved from Office 365 Import window. And will leave all the logs in your local drive c:\PSTupload\Uploadlog.log
AzCopy /Source:C:\Users\Mohammed\Desktop\upload /Dest:https://d49d7ae0e38a4d8e9c93565.blob.core.windows.net/ingestiondata/SERVER01/PSTshareR1/ /Destkey:KA9Z00rEYa1JlqGE4wO222MnsN5ywT0elOgLeNht/fSMIJPe2134hEChuuDJ5mfdknq8ts0+cez6uUvFzcQd6g== /S /V:C:\PSTUpload\Uploadlog.log
![clip_image005[4]](http://lh3.googleusercontent.com/-ODWqZPIOLME/VcPSsWYgrMI/AAAAAAAAQkM/SliRrYjrn6c/clip_image005%25255B4%25255D_thumb.png?imgmax=800)
To make sure that files are uploaded. I will open Azure Storage Explorer 6 (Preview) and click Add Account on top
On add storage account window I will use the blob name that I have got from the URL earlier and storage secure key in the storage account key below and click on save.
![clip_image006[4]](http://lh3.googleusercontent.com/-qZ1xjhXciKQ/VcPSuGNolmI/AAAAAAAAQkc/vxM0mYHmZLs/clip_image006%25255B4%25255D_thumb.png?imgmax=800)
Once I click that I will get a list of directories, The default directory which is used by Office 365 is the “Ingestiondata” folder, There our files will be uploaded.
![clip_image007[4]](http://lh3.googleusercontent.com/-tJP9TFO2rXc/VcPSvoFmSCI/AAAAAAAAQks/arVuBtEY1OE/clip_image007%25255B4%25255D_thumb.png?imgmax=800)
https://azure.microsoft.com/en-us/documentation/articles/storage-use-azcopy/
4. Create CSV File to import PST
Assuming you have 150 PST files that you want to upload and import into users which already have been enabled on Exchange online … In order to do so you will have to prepare a CSV file that looks like the below sample
To provide an explanation of what each column stands for .. Microsoft has written a table that clears the dust but some parts were not even clear for me like the FilePath as in the TechNet article it gets you confused with the “Ship data on Physical hard drives” since it uses your drive to upload data directly to Azure through the Import tool on Office 365 portal.

Note:
The friendly path here is the path of the folder you have created in Azure through the Azcopy command
AzCopy /Source:C:\Users\Mohammed\Desktop\upload /Dest:https://d49d7ae0e38a4d8e9c93565.blob.core.windows.net/ingestiondata/SERVER01/PSTshareR1/
/Destkey:KA9Z00rEYa1JlqGE4wO222MnsN5ywT0elOgLeNht/fSMIJPe2134hEChuuDJ5mfdknq8ts0+cez6uUvFzcQd6g== /S /V:C:\PSTUpload\Uploadlog.log
CSV Sample
![clip_image008[4]](http://lh3.googleusercontent.com/-lV8HzA24Ftg/VcPSyywSPJI/AAAAAAAAQlM/1hu6ds4yvnw/clip_image008%25255B4%25255D_thumb.png?imgmax=800)
So the CSV File is ready.
In Azure Storage Explorer I doubled check if the PST files has finished uploading and it’s there.
![clip_image009[4]](http://lh3.googleusercontent.com/-bjB8dS5eleo/VcPS1FVAFEI/AAAAAAAAQlc/WMH7BtuFefg/clip_image009%25255B4%25255D_thumb.png?imgmax=800)
5. Using the Upload Files over the network
Back to Office 365 portal, go to Import and click on the + Sign and select Upload files over the network
![clip_image010[4]](http://lh3.googleusercontent.com/-cuWPEDgmqXw/VcPS2cXKWhI/AAAAAAAAQls/PluTznlZ9wY/clip_image010%25255B4%25255D_thumb.png?imgmax=800)
Select I have access to the mapping file as well
![clip_image011[4]](http://lh3.googleusercontent.com/-XN6qGtUag_c/VcPS4SiDlzI/AAAAAAAAQl8/fVxhTgdyAbU/clip_image011%25255B4%25255D_thumb.png?imgmax=800)
Click on + and upload the CSV file that you have prepared for the mapping
Next File is imported, Click on “By checking this box, you agree to the terms and conditions of this service.
![clip_image012[4]](http://lh3.googleusercontent.com/-2B9g7XGsUJQ/VcPS6bCqwdI/AAAAAAAAQmM/wqtKgo14JPw/clip_image012%25255B4%25255D_thumb.png?imgmax=800)
As soon as you accept and click next the Import is going to check path, email, folder and will start the import process.
![clip_image013[4]](http://lh3.googleusercontent.com/-SzT14seXOBw/VcPS7072B2I/AAAAAAAAQmc/TRawO6qu8a4/clip_image013%25255B4%25255D_thumb.png?imgmax=800)
![clip_image014[4]](http://lh3.googleusercontent.com/-99Ic13O-dkI/VcPS9vQu07I/AAAAAAAAQms/6p5GQOVYOs4/clip_image014%25255B4%25255D_thumb.png?imgmax=800)
Email before importing
![clip_image015[4]](http://lh3.googleusercontent.com/-39KkXnOmQRk/VcPS_psRBMI/AAAAAAAAQm8/b6HpTvRPnwY/clip_image015%25255B4%25255D_thumb.png?imgmax=800)
Imported started, folder has been created
![clip_image016[4]](http://lh3.googleusercontent.com/-mXjyrobyXkE/VcPTBLo-mxI/AAAAAAAAQnM/Rviq0bD9Pvs/clip_image016%25255B4%25255D_thumb.png?imgmax=800)
Importing is done
![clip_image017[4]](http://lh3.googleusercontent.com/-eyG-V8SPVUw/VcPTD_mlY_I/AAAAAAAAQnc/CUerGsYMID8/clip_image017%25255B4%25255D_thumb.png?imgmax=800)
‘
![clip_image018[4]](http://lh3.googleusercontent.com/-mfjSWmecuEM/VcPTF_qD8YI/AAAAAAAAQns/s0ACoW4k-Nc/clip_image018%25255B4%25255D_thumb.png?imgmax=800)
Importing is done
Reference
https://azure.microsoft.com/en-us/documentation/articles/storage-use-azcopy/














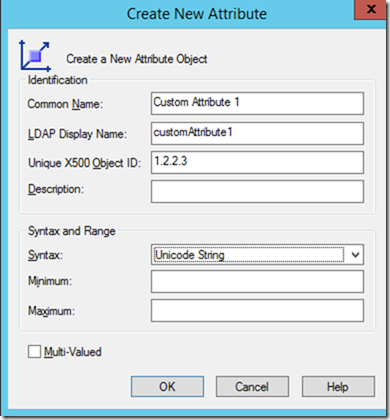




![clip_image001[5]](http://lh6.ggpht.com/-bTsYbCoyBDE/VSe6tby9vwI/AAAAAAAAORQ/7oMFwn6XVWs/clip_image001%25255B5%25255D_thumb.png?imgmax=800)
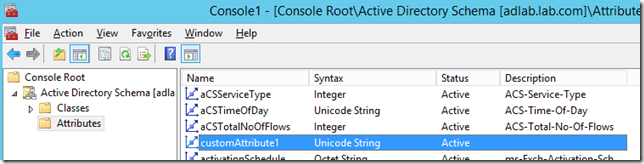
![clip_image002[4]](http://lh4.ggpht.com/-Tc_IjdCkie4/VSe6vTh70nI/AAAAAAAAORg/DaVeYIKS1F4/clip_image002%25255B4%25255D_thumb.png?imgmax=800)
![clip_image003[4]](http://lh4.ggpht.com/-5paj8WsOWZs/VSe6xkWuhKI/AAAAAAAAORw/ZkFYGWVxNeM/clip_image003%25255B4%25255D_thumb.png?imgmax=800)
![clip_image004[4]](http://lh4.ggpht.com/-dn2f9cdUKEo/VSe60bcnjYI/AAAAAAAAOSA/du-W37Jv-jM/clip_image004%25255B4%25255D_thumb.png?imgmax=800)
![clip_image005[4]](http://lh6.ggpht.com/-pnvgRPt6_n4/VSe62yUPVgI/AAAAAAAAOSQ/P5WUuU98X90/clip_image005%25255B4%25255D_thumb.jpg?imgmax=800)
![clip_image006[4]](http://lh5.ggpht.com/-lg6fVFgFc8o/VSe65oCP2kI/AAAAAAAAOSg/8ouI0xFaxPY/clip_image006%25255B4%25255D_thumb.jpg?imgmax=800)