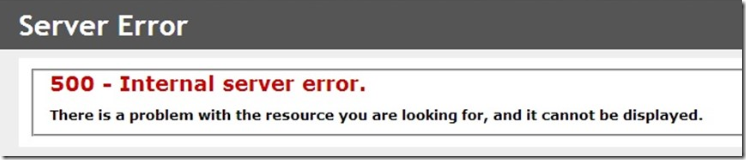
Error code
Yesterday my colleague sent me a message informing me that ADFS is not working. When I tried to login to Office 365 Portal page with a federated domain’s user I got a 500 Internal Server Error.
When it occurs:
If you are using Office 365 with ADFS Integration in place, You might get this error when trying to authenticate your users to login to Office 365 or any of its services.
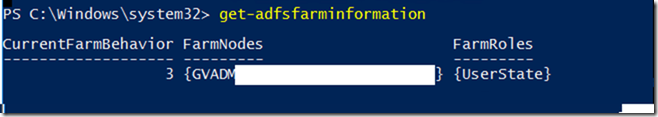
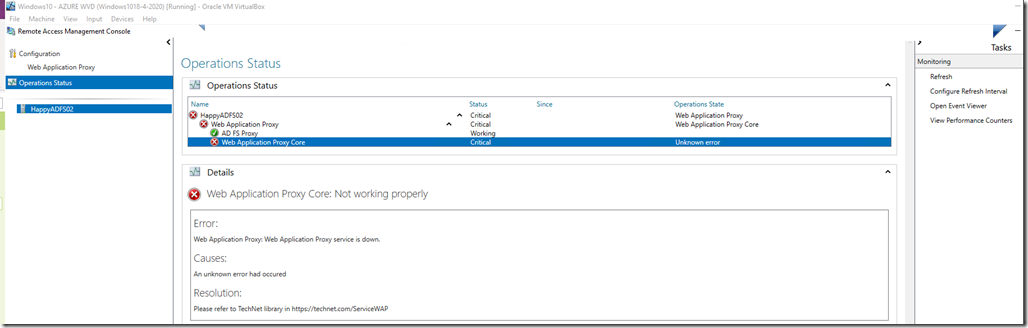
WAP Server
In this environment I am using WAP Proxy server behind ADFS and when installing this I configured a trust using a Public Certificate but for some reason this trust was broken.
Investigation and Solution:
After investigating the WAP proxy it seems it had couple of problems:
1- Could not resolve ADFS server name on WAP Server.
- In my environment where we are using Sentinel, We have isolated the primary DC in the environment and due to this the WAP server could not reach to the DNS Server. I solved this by pointing the machine to the secondary DC and add the ADFS hostname to the host file.
2- The Web Application Proxy Service would not start.
- The errors related to the service not starting in the event viewer were all pointing to a certificate thumbprint which didn’t even exist in the WAP’s personal store.
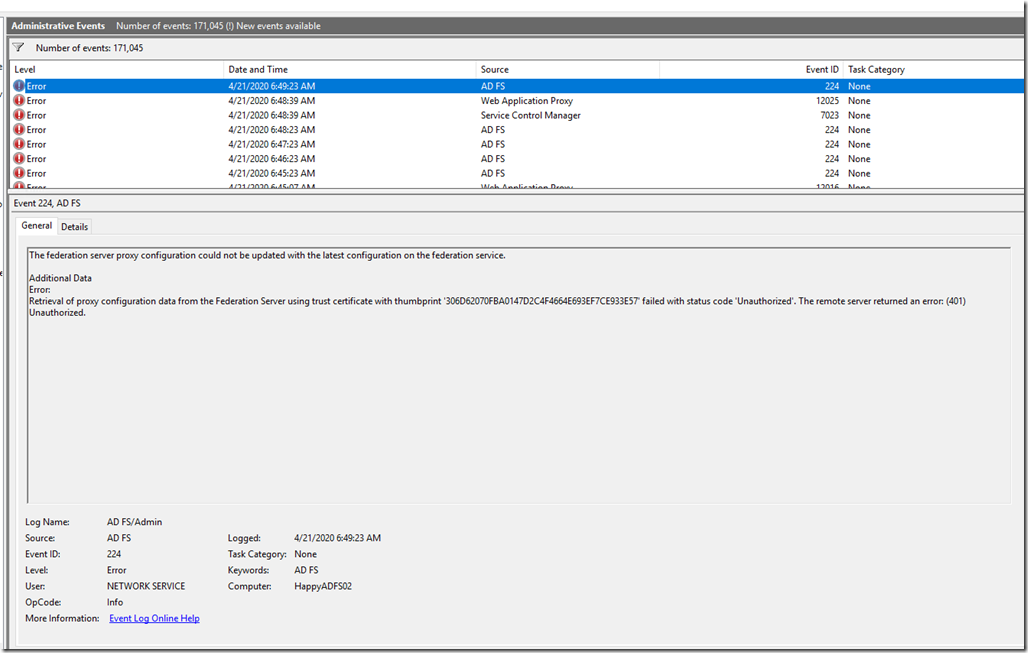
Event Viewer Errors
There were couple of errors related to the certificate and Service issue, Event ID 224, Event ID 12025, Event ID 7023 and Event ID 224.
The one which mostly got my attention was the 224:
The federation server proxy configuration could not be updated with the latest configuration on the federation service.
Retrieval of proxy config data from federation server using trust certificate with thumbprint failed with status code unauthorized. The remote server returned an error code 401.
Resolution:
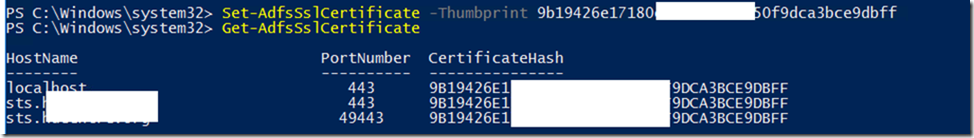
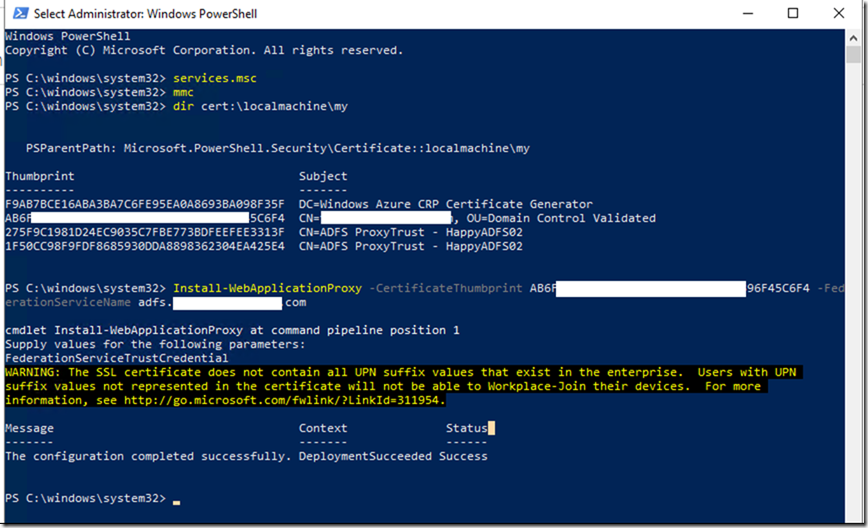
From WAP server’s fire up PowerShell as an admin and list the certificate you have got on your Personal store and match the ThumbPrints of the certificate in the error to make sure it exists or not.
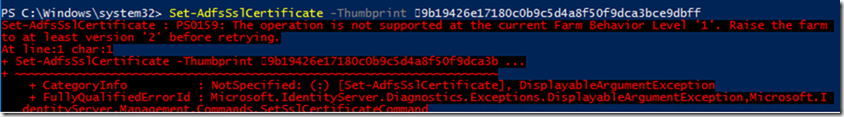
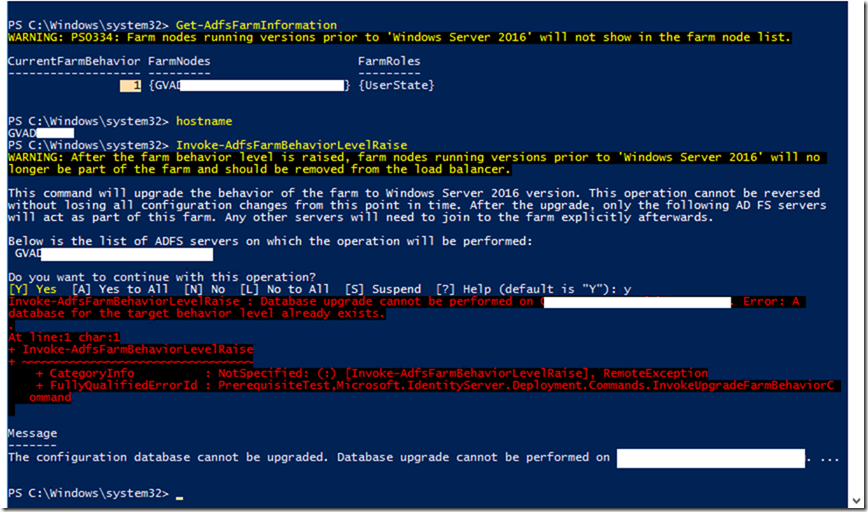
Even if the certificate exists you will still need to re-establish trust with ADFS to make sure WAP can connect to ADFS without an issue.
Dir Cert:\localmachine\my
This should show the certificates you have got on your store.
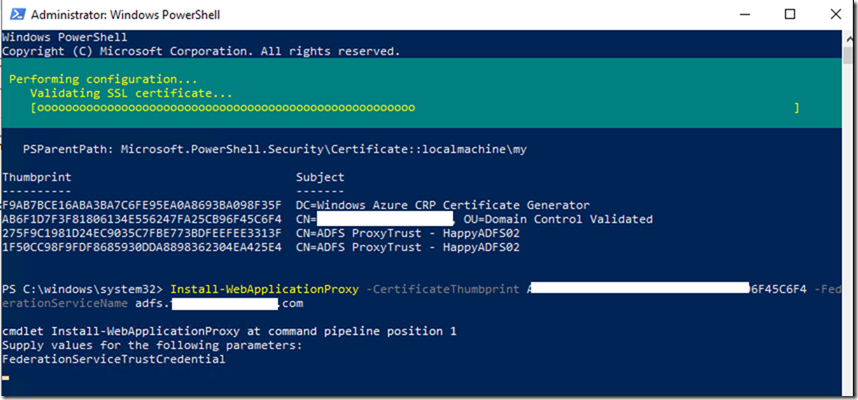
Now pick up the valid Public certificate which you want to use for the trust and use the below command to establish the trust
Install-WebApplicationProxy –CertificateThumbprint “Enter Certificate ThumbPrint here” –FederationServiceName “ADFS Public FQDN Here”
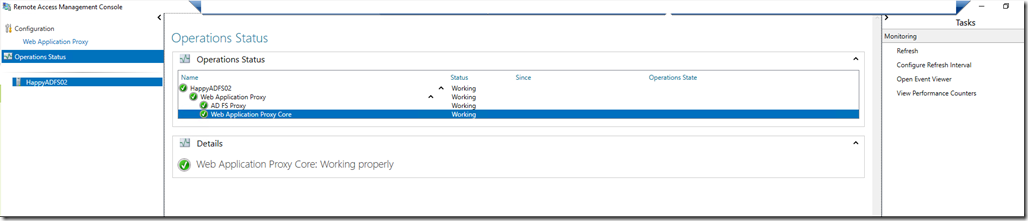
After few moments you should see that WAP services went back to normal and you can now login your users to Office 365 portal through ADFS.
![clip_image001[6] clip_image001[6]](https://www.moh10ly.com/wp-content/uploads/2020/04/clip_image0016_thumb.png)
![clip_image001[4] clip_image001[4]](https://www.moh10ly.com/wp-content/uploads/2020/01/clip_image0014_thumb.png)
![clip_image001[6] clip_image001[6]](https://www.moh10ly.com/wp-content/uploads/2020/01/clip_image0016_thumb.png)