Setting up UM
To setup UM between Exchange and Skype for business server, the most important step is how you configure the Certificates between both servers in order for them to trust each other.
For that you don’t have to use a public Certificate but rather an internal CA certificate that has its root certificate installed on all of the server where you intend to deploy the UM. (Exchange, S4B Servers..etc.).
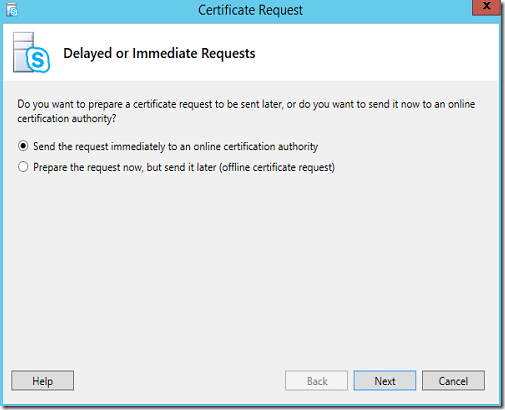
To claim this certificate, the easiest step would be to get the CSR from Skype for Business’s Deployment Wizard
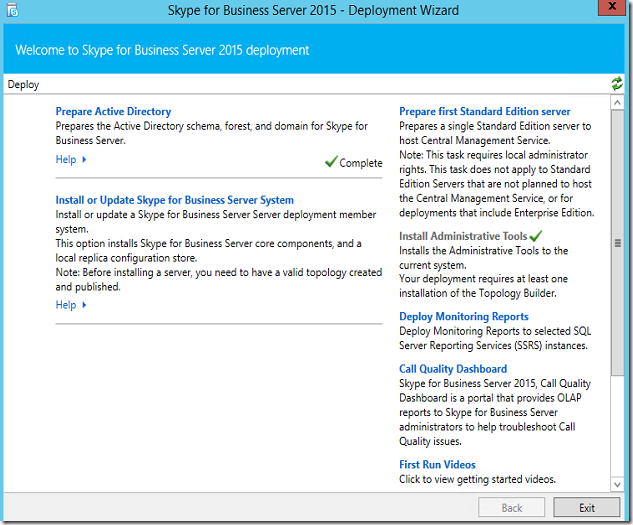
Run Deployment Wizard and click on the “Install or Update skype for business Server system”
Then click on step 3 (request, install or assign Cert)
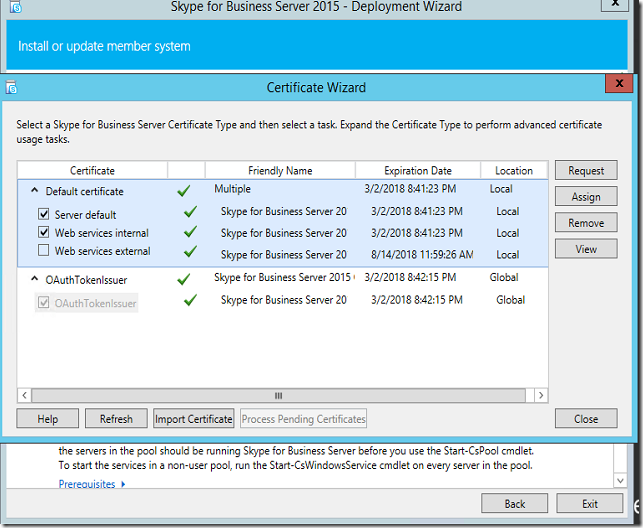
I already have certificate deployed for S4B service but I’ll request CSR again to get one trusted certificate for both Exchange and S4B.
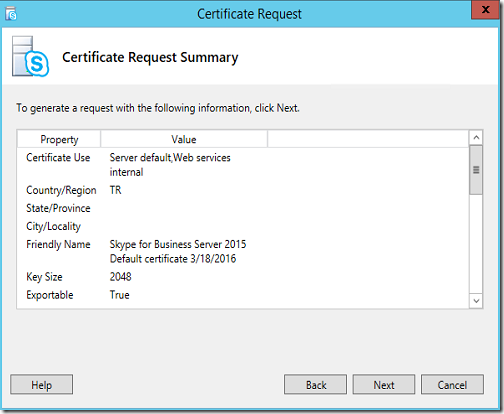
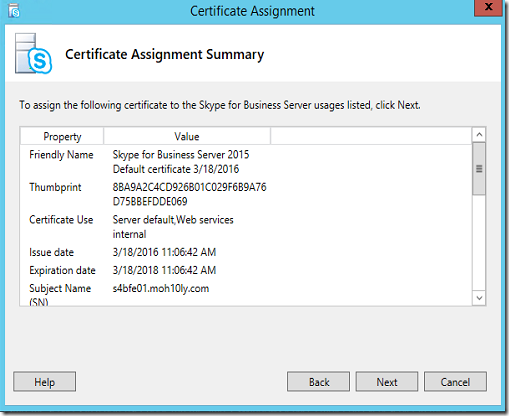
I will tick only the services that matters as in the below screenshot (Server default and Web services internal) later also will be used for OWA integration with UM.
Click on Request
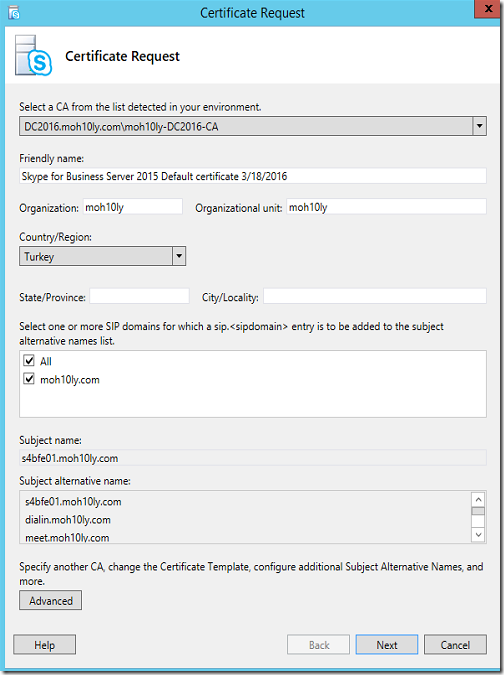
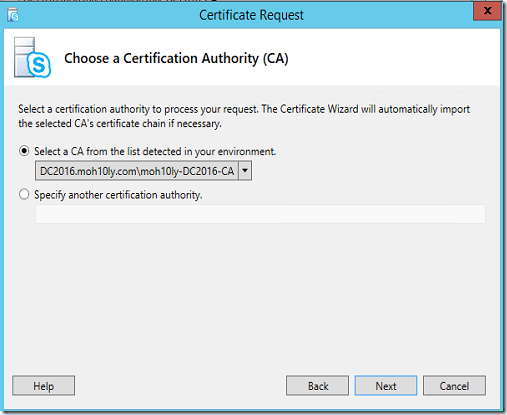
Click on Advanced
Next
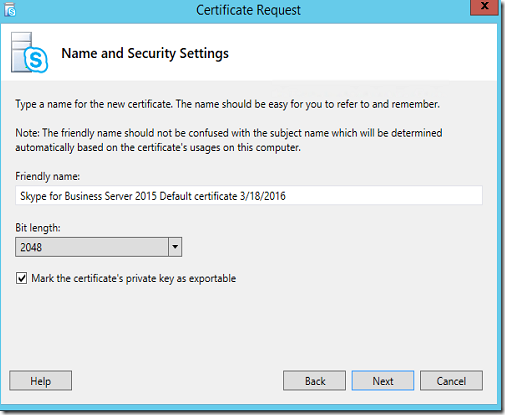
I’ll continue next until I’ve got to the important part which is “Name and Security settings” I’ll need to tick the “Mark the certificate’s private key as exportable” since we’ll export the certificate to Exchange servers
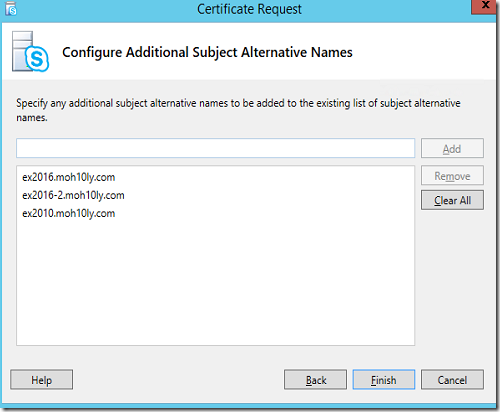
Next I’ll add Exchange servers’s FQDNs.
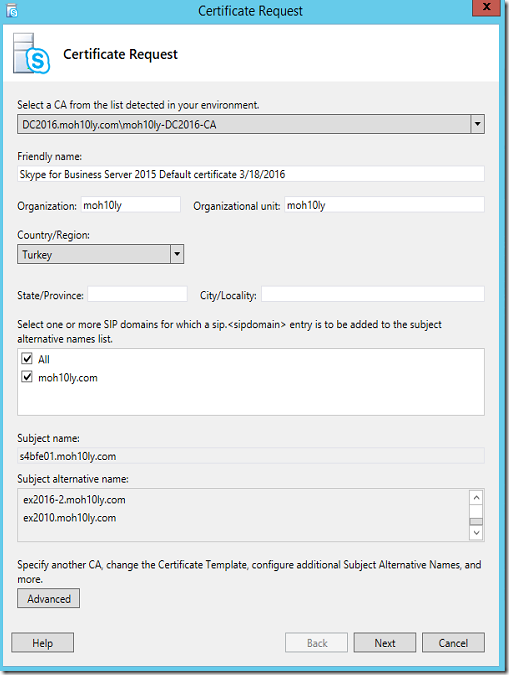
Click Next
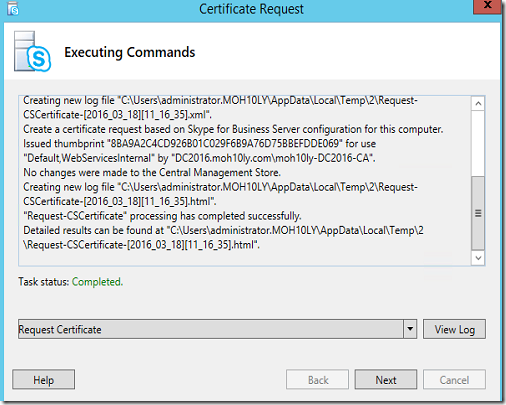
Here is the CMDLET
Request-CSCertificate -New -Type Default,WebServicesInternal -CA “DC2016.moh10ly.com\moh10ly-DC2016-CA” -Country “TR” -FriendlyName “Skype for Business Server 2015 Default certificate 3/18/2016” -KeySize 2048 -PrivateKeyExportable $True -Organization “moh10ly” -OU “moh10ly” -DomainName “sip.moh10ly.com,ex2016.moh10ly.com,ex2016-2.moh10ly.com,ex2010.moh10ly.com” -AllSipDomain -Verbose -Report “C:\Users\administrator.MOH10LY\AppData\Local\Temp\2\Request-CSCertificate-[2016_03_18][11_16_35].html”
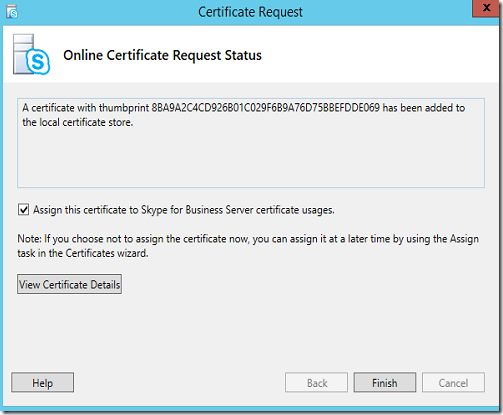
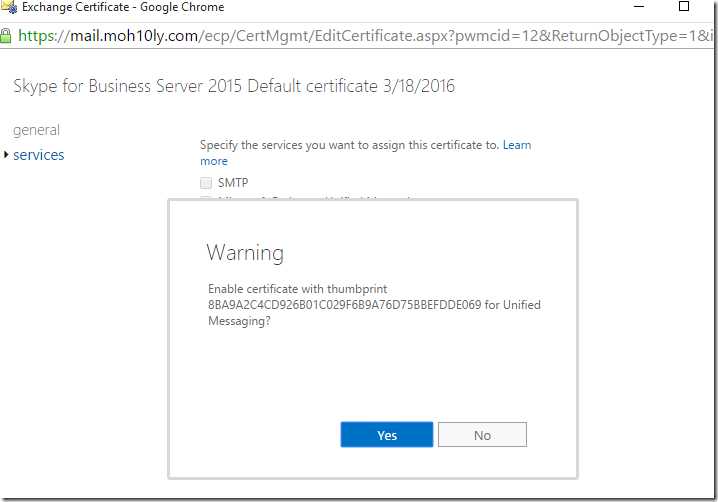
Click Next again and mark the thumbprint for the new Cert as we’ll need to see it later to make sure it’s properly configured for the UM on Exchange.
8BA9A2C4CD926B01C029F6B9A76D75BBEFDDE069
Click next to assign the Cert
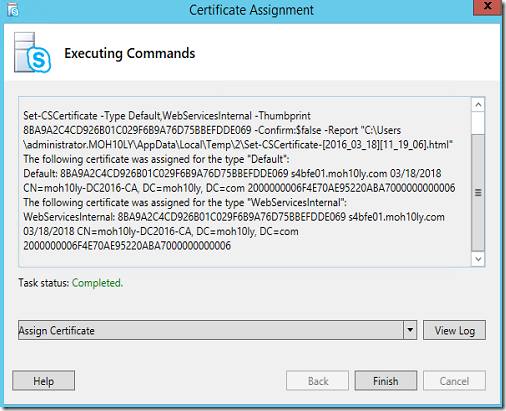
Successfully, the certificate has been assigned to the Services
The CMDLET that was applied
Set-CSCertificate -Type Default,WebServicesInternal -Thumbprint 8BA9A2C4CD926B01C029F6B9A76D75BBEFDDE069 -Confirm:$false -Report “C:\Users\administrator.MOH10LY\AppData\Local\Temp\2\Set-CSCertificate-[2016_03_18][11_19_06].html”
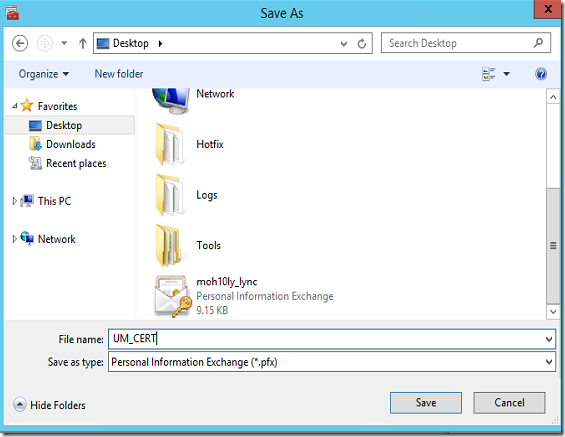
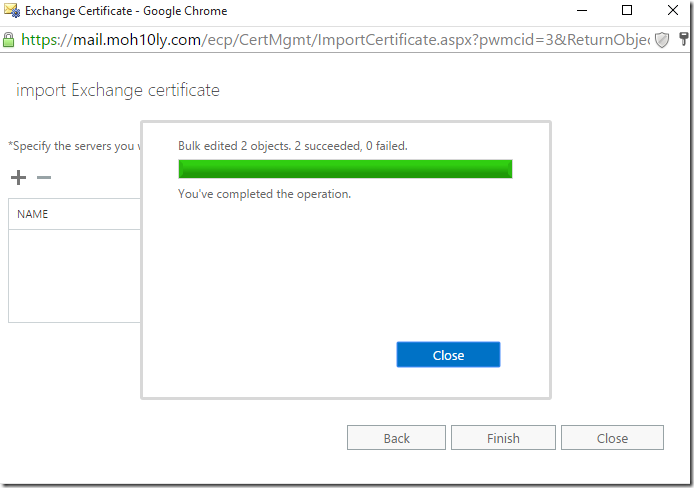
Now it’s time to export this certificate and import it to Exchange servers
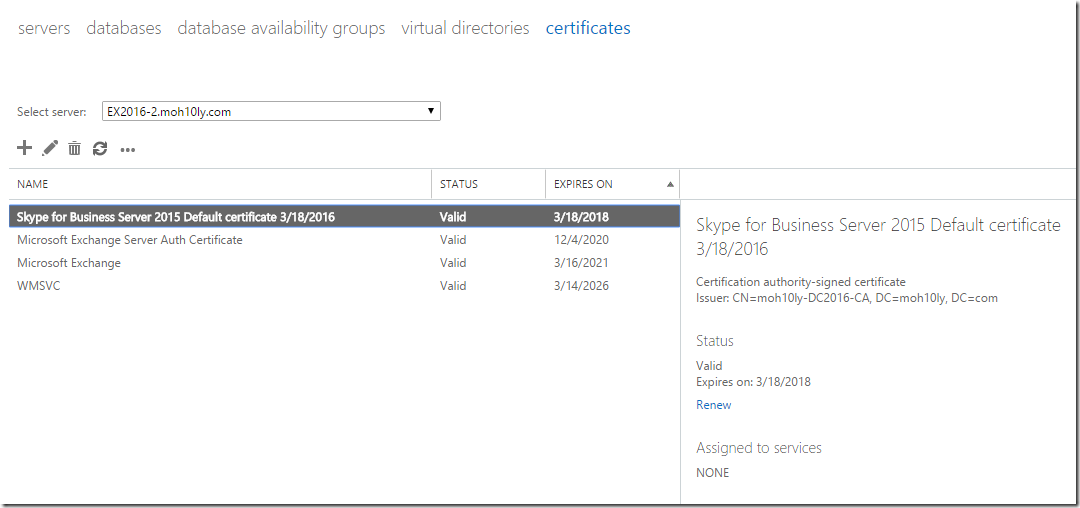
I’ll find the certificate that I have created today by looking at the expiration date which is 2 years from now with the same day.
Now I’ll right click on the certificate and export it with the private key.
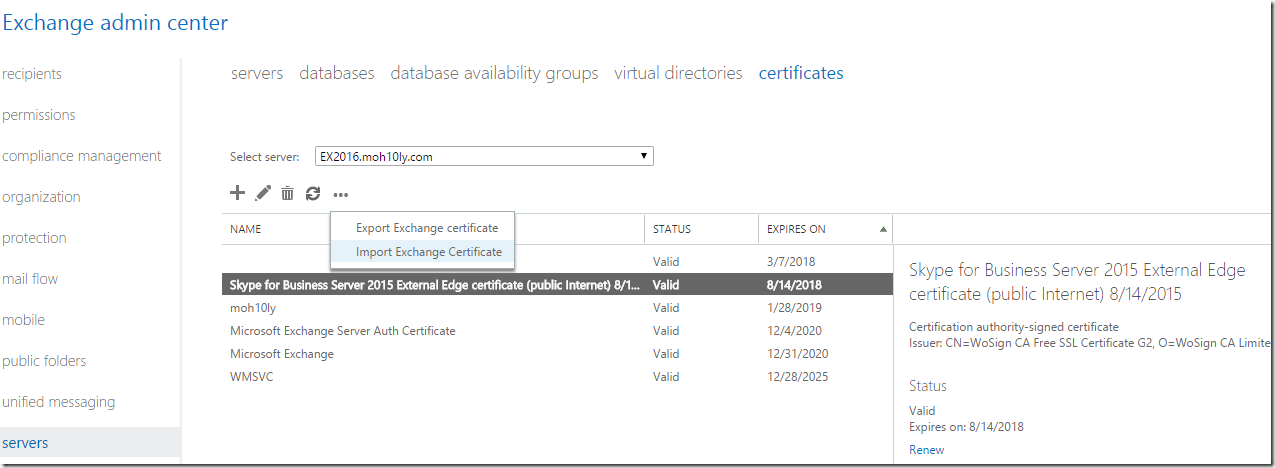
I’ll open Exchange EMC and import the certificate
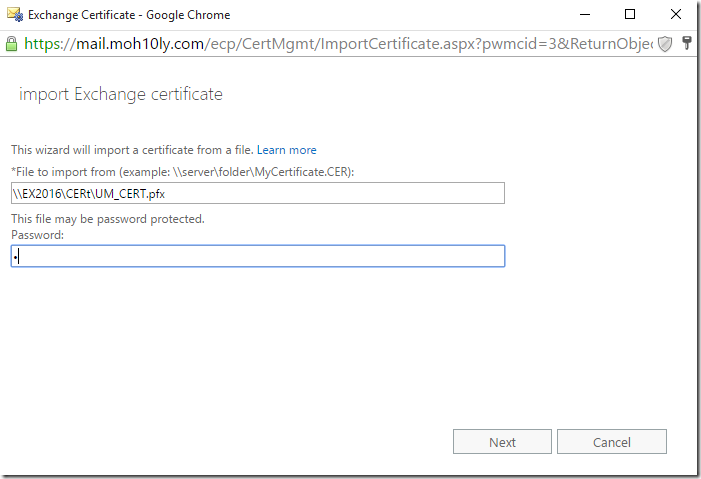
I’ll have to put the exported cert in a shared folder and provide the path and the password for it
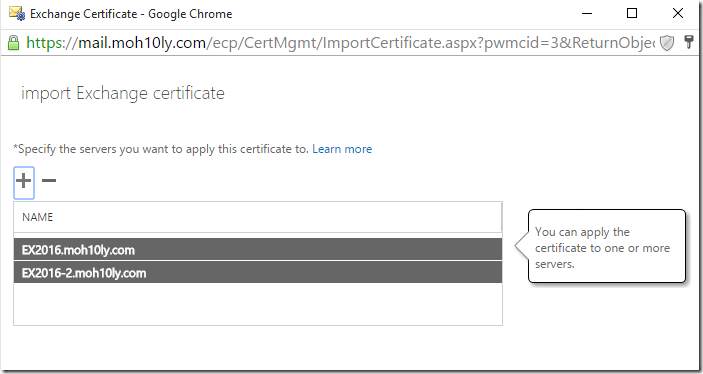
I’ll add the two servers below
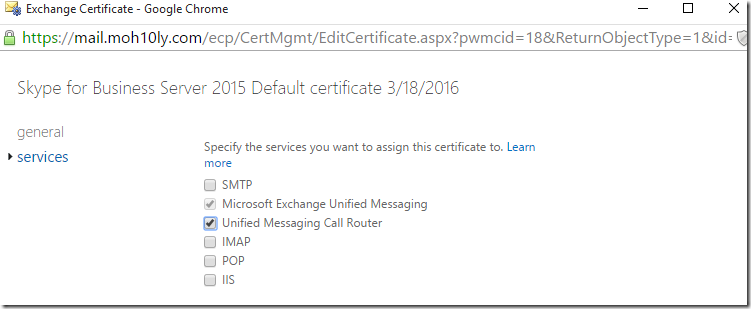
I’ll double click on the imported certificate and assign the UM services to it on each of the servers
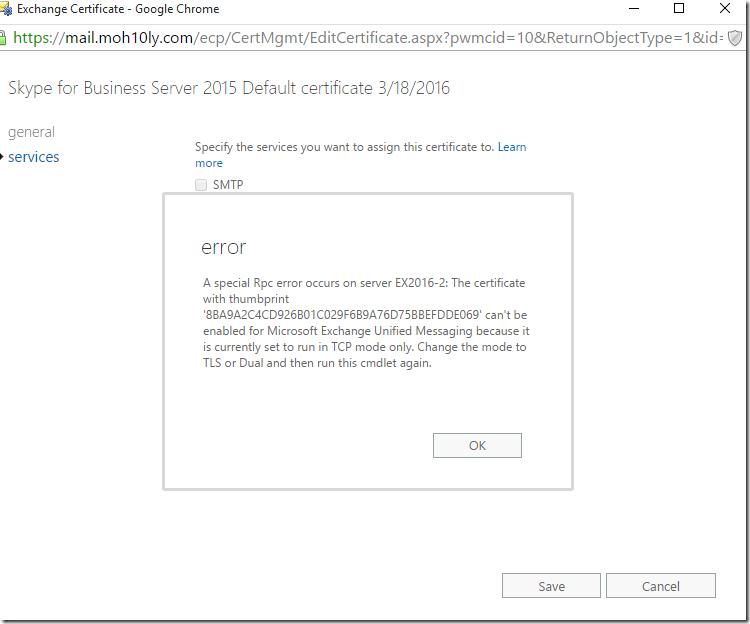
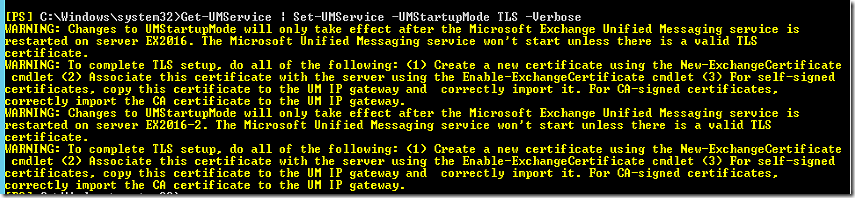
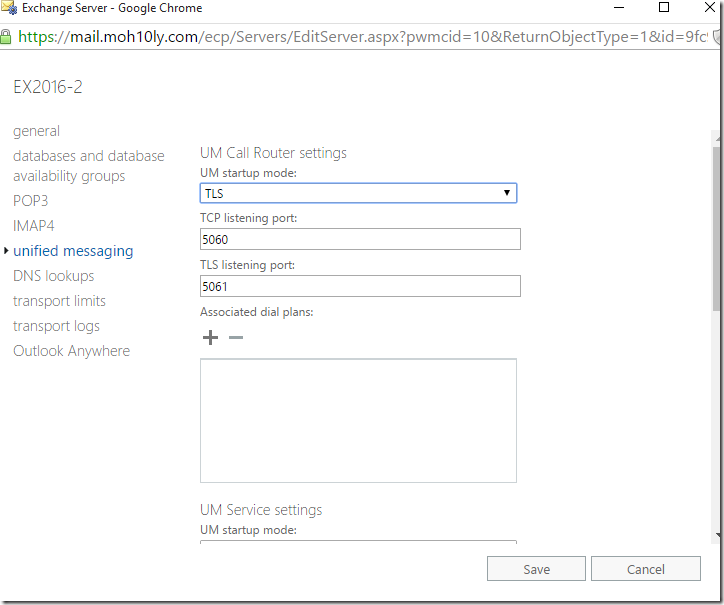
I have got the below error due to not configuring the service to use TLS instead of TCP on both servers.
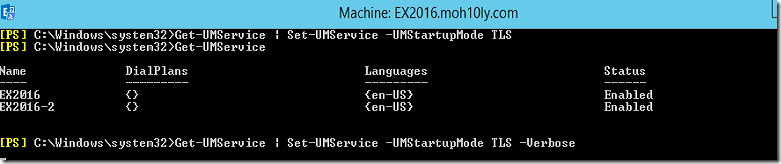
To fix this I’ll go on Exchange Management shell and run the following CMDLET
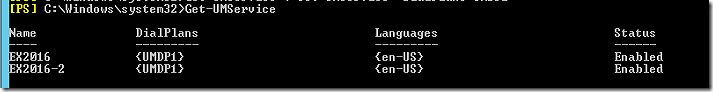
Get-UMService | Set-UMService -UMStartupMode TLS
Now I’ll try to save again
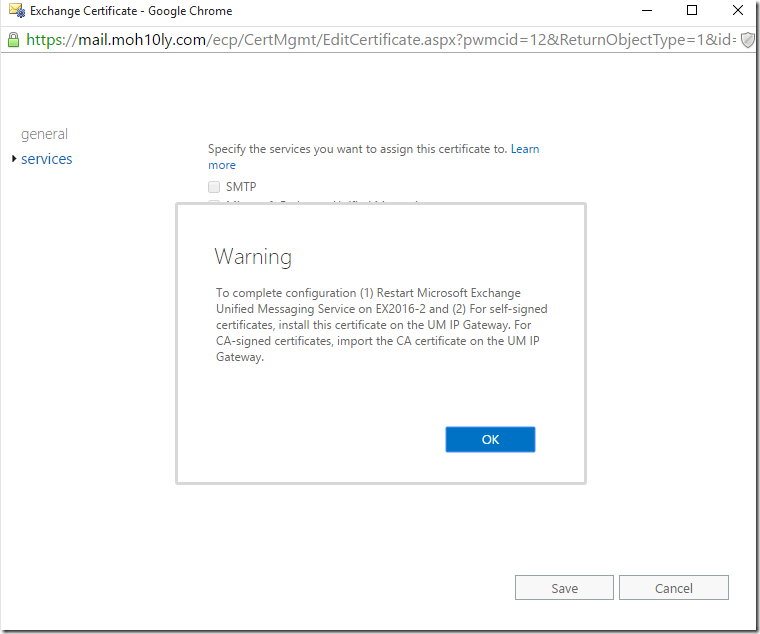
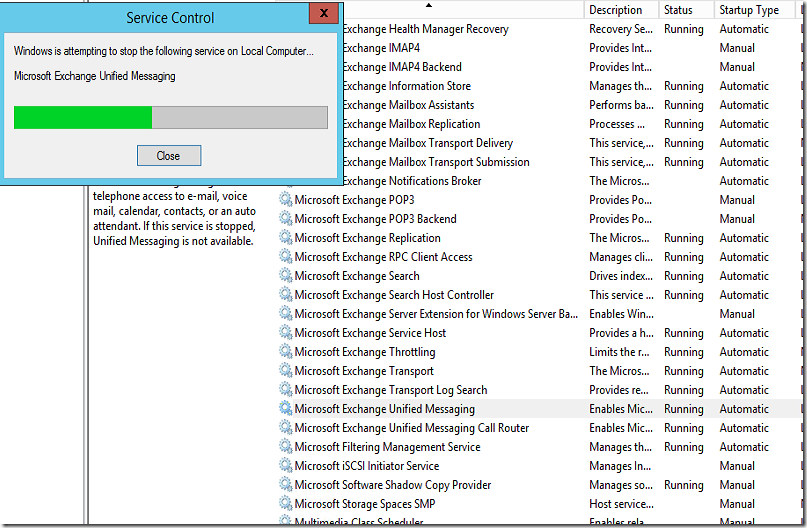
I’ll proceed with YES and continue to do the same to the other Server and restart the UM service on both servers
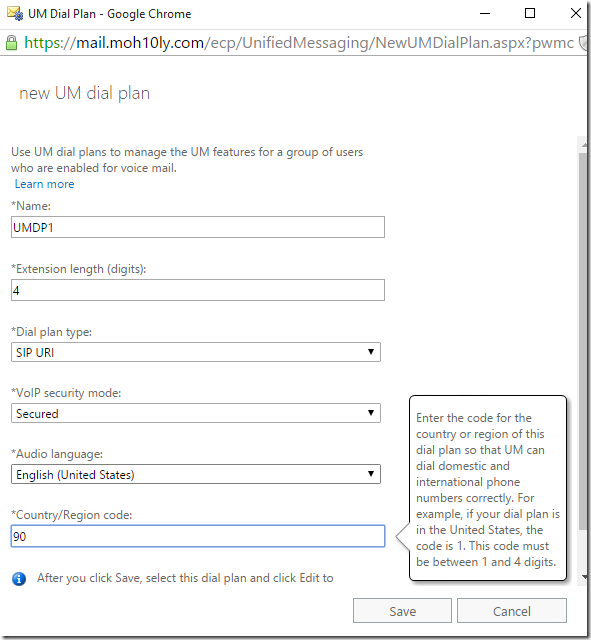
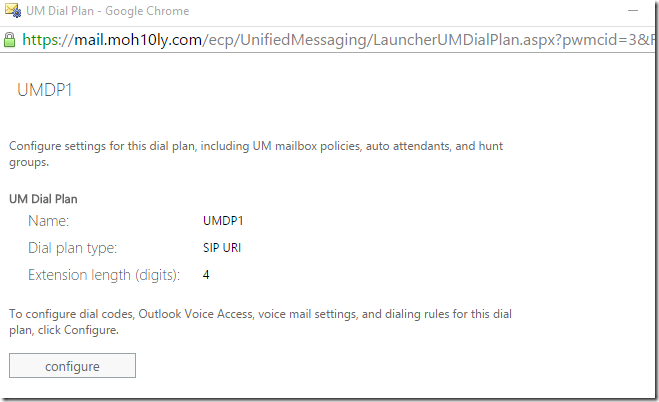
Now it’s time to create a UM Dial plan
I’ll configure the UM Dial plan according to my Skype for Business settings for users enabled for EV
To use powershell, you can use the following cmdlet
New-UMDialPlan –Name DialplanName –UriType SIPURI –NumberOfDigitsInExtension 4 –VoIPSecurity Secured –CountryOrRegionCode 1 –AccessTelephoneNumber +9012345678
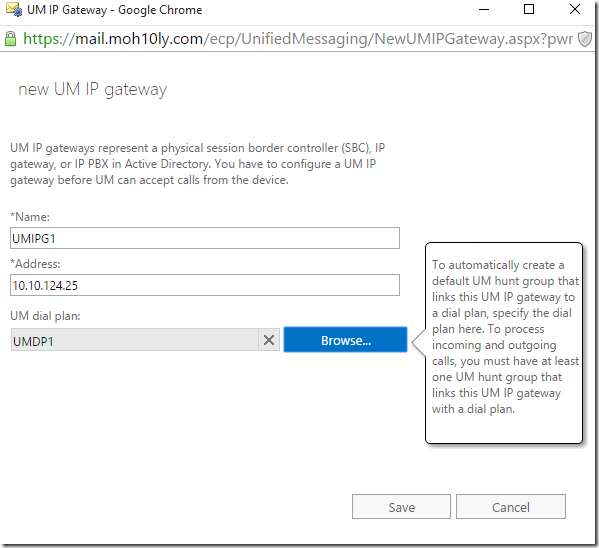
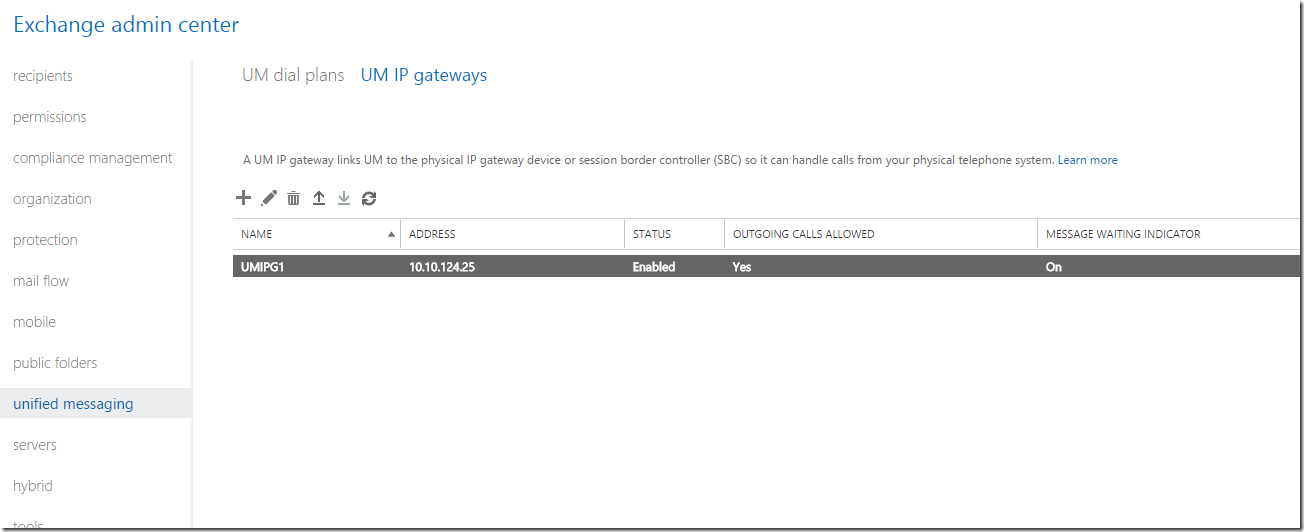
Next, adding a gateway to the UM (NOTE: If configured incorrect, will cause the service not to start and errors with event ID (1057, 4999,1430, 1038) will appear.
Time to configure Gateway
In the gateway I’ll add my PBX (AsteriskNow) and place my already configured UMDP
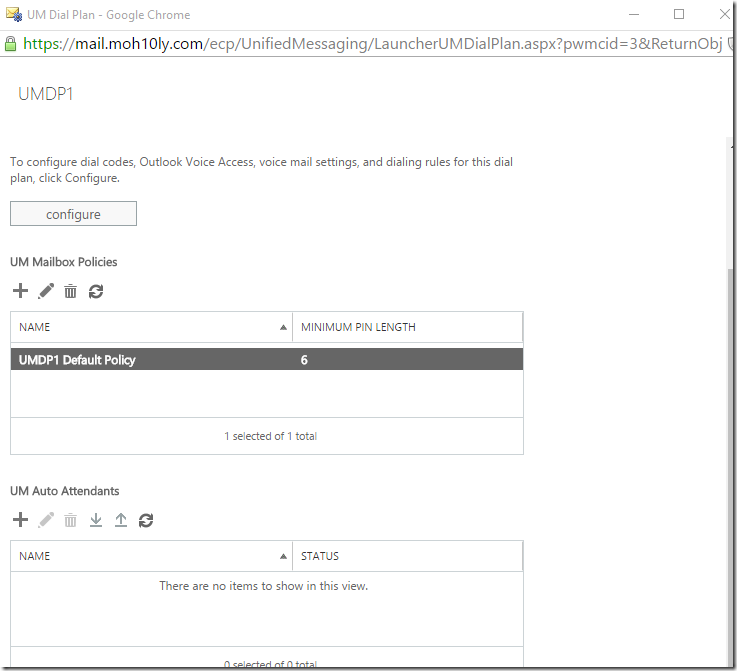
When you create the dial plan, Exchange automatically creates a new UM mail policy along with it and it also generates a name that’s related to the Dial plan
In order to see this policy, you will have to double click on the new dial plan to view it and you can also change the policy in it .. Which I’m going to apply for the length of the policy to make it shorter
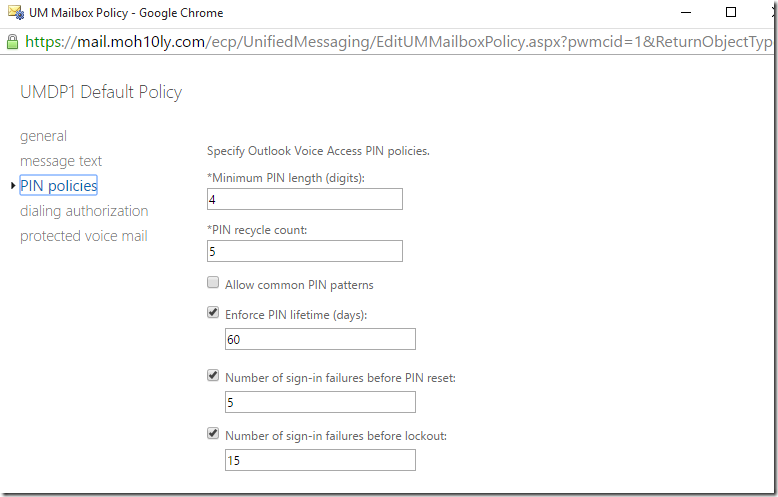
Double click on the Mailbox policy and navigate to Pin Polices and change it to the length you want to allow
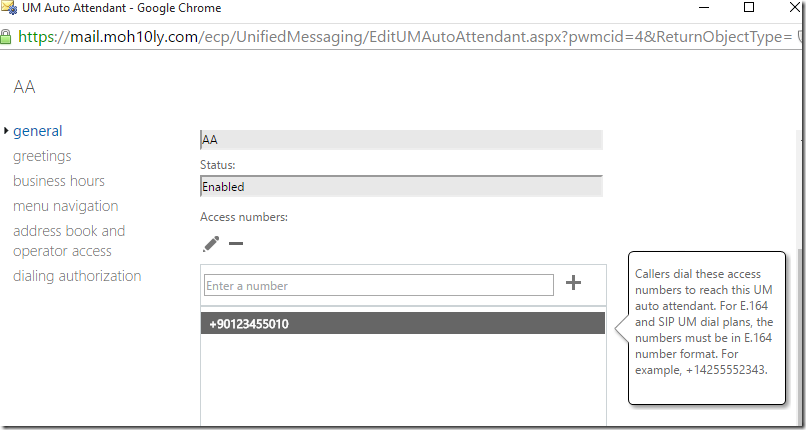
Configure Auto Attendant
Set the AA as how you want it to be configured and make sure you add the full E.164 format as it won’t accept otherwise.
Click Save to continue
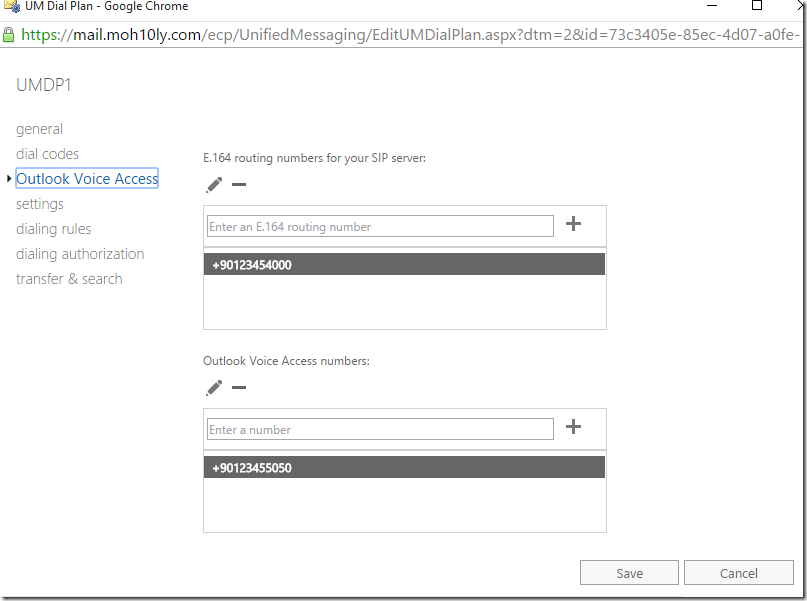
Now time to configure OVA (Outlook voice access)
Subscriber Access
If you want to configure Outlook Voice Access (OVA) , sometimes also referred to as Subscriber Access, click on the Configure button. Select Outlook Voice Access in the left hand menu and enter the telephone number you want to use to access OVA. This must be in the E.164 notation.
To do so click on Configure
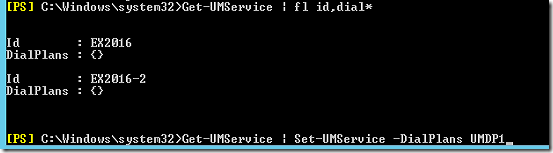
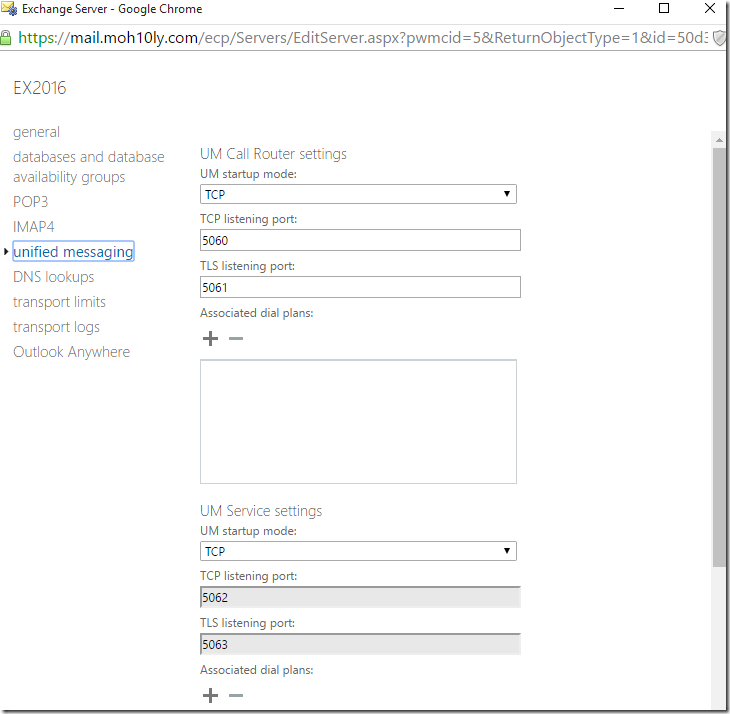
To assign the new dial plan to the UM services, both on the Client Access Server (UM Call Router) as well as on the Mailbox server. In an Exchange Management Shell windows enter the following commands:
1
2
Set-UMCallRouterSettings -DialPlans “Exchangelabs Dial Plan” –Server 2012E15FE04
Get-UMService | Set-UMService -DialPlans “Exchangelabs Dial Plan”
Now I’ll also change the UM call router to TLS and assign Certificate to the service then restart it
Restart the services of the Call router, then associate the service with the dialplan you created.
Set-UMCallRouterSettings -DialPlans “UMDP1” –Server EX2016
Set-UMCallRouterSettings -DialPlans “UMDP1” –Server EX2016-2
Configure Skype for Business Server
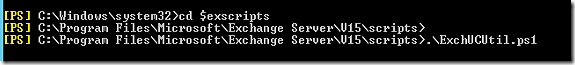
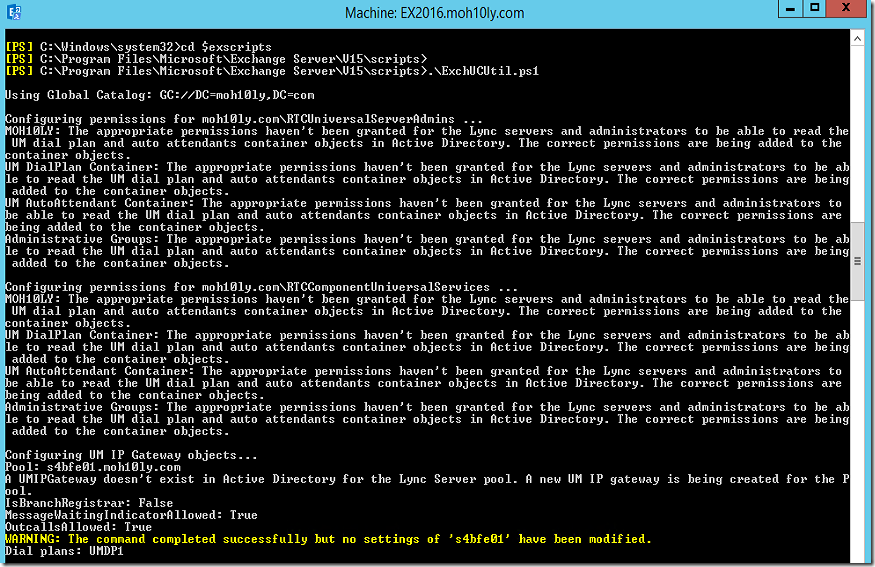
To configure the UM Service to be used with Skype for Business Server. Microsoft has a script that will create and configure all necessary components. This scripts is located in the scripts directory C:\Program Files\Microsoft\Exchange Server\V15\Scripts.
Run the following CMDLET
CD $ExScripts
.\ExchUCUtil.ps1
The first time you setup this script it’ll detect the Dial plan and set it up with Skype for Business Server
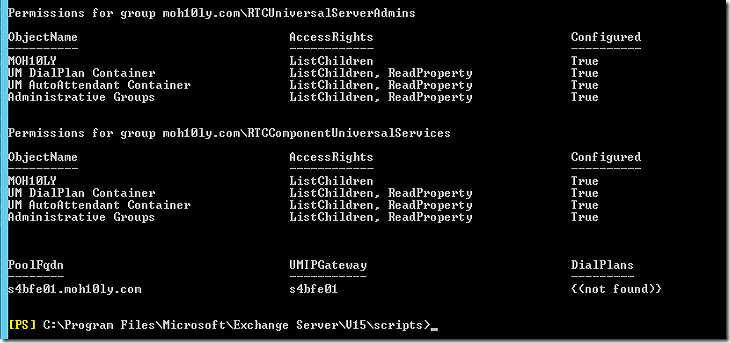
It will show that no setting has changed but the fact that the dial plan is showing here Not found means that there something has changed .. You’ll notice that if you run the same script again.
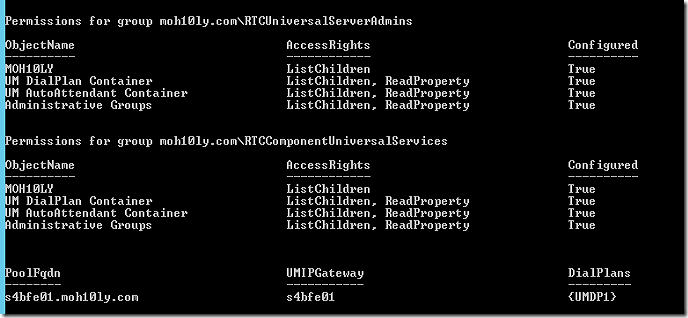
Let’s try it again
Here you can see that the dial plan has been assigned to the S4B Front end server.
This script performs the following:
- Grants Skype for Business Server permission to read Exchange UM Active Directory components, specifically, the SIP URI dial plan that was created in the first step;
- Creates a UM IP gateway for each Skype for business Server pool that hosts users who will be enabled for Enterprise Voice;
- Create an Exchange UM hunt group for each UM IP gateway. The hunt group pilot identifier will be the name of the dial plan associated with the corresponding UM IP gateway. The hunt group must specify the UM SIP dial plan used with the UM IP gateway.
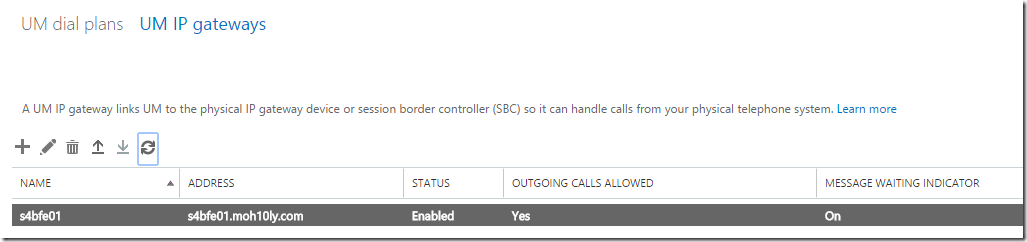
When the script has run you’ll see a new UM IP Gateway appear in the EAC. Since this script not only creates the UM IP Gateway but also sets the necessary permissions the UM IP Gateway was not created manually in the first step.
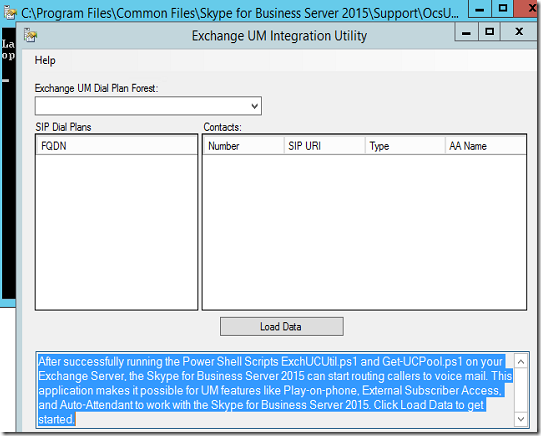
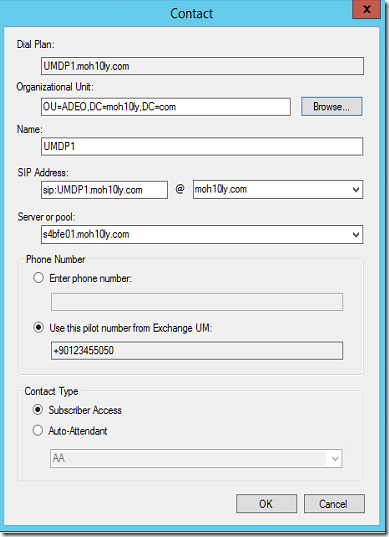
Next we’ll go to Skype for Business FE server and then run the OcsUmUtil.exe tool which creates the contact objects for Outlook Voice Access and for the auto attendants. This tool can be found in C:\Program Files\Common Files\Skype for Business Server 2015\Support
I’ll right click the file to run it as administrator
Click on Load Data
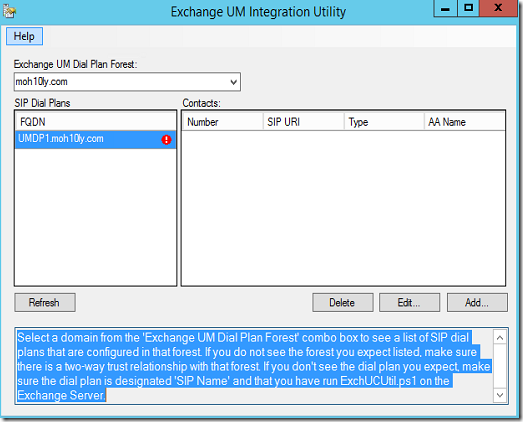
Select the SIP dial plan and click ADD
Click OK
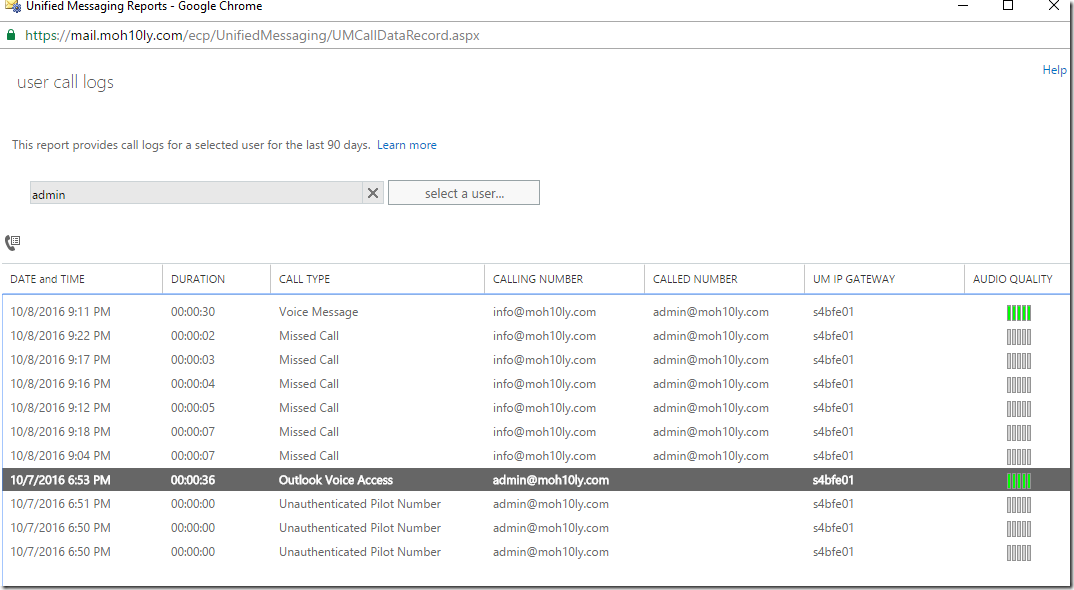
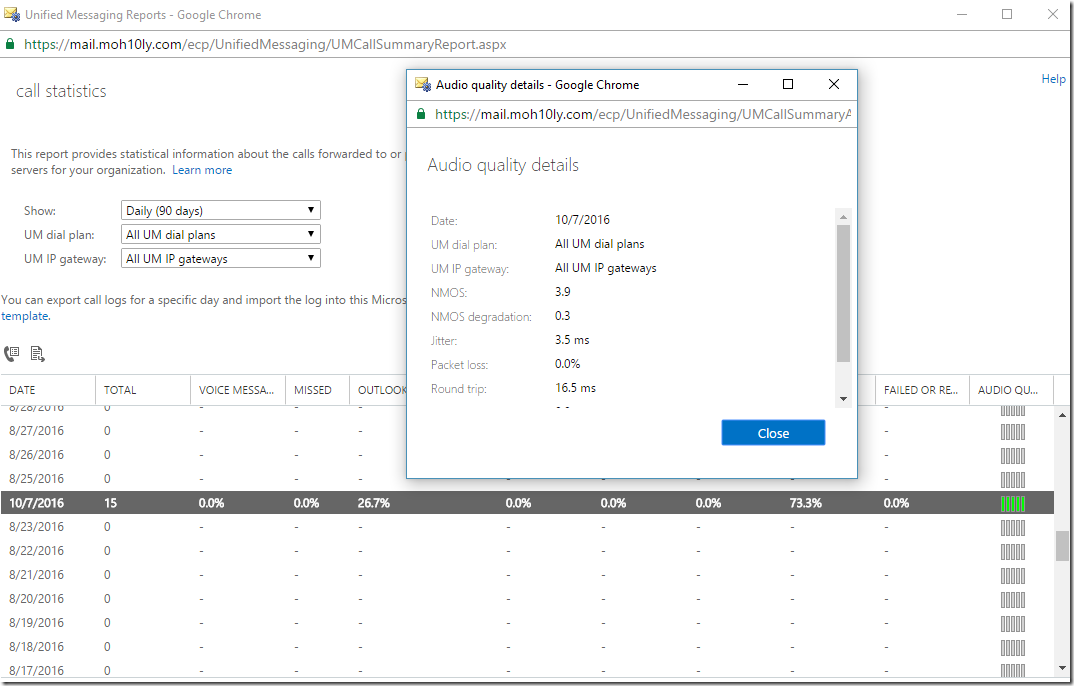
Right after configuring this your Voice mail should be enabled once you enable your user for it
After I enable user for UM and assign a valid dialplan .. Now I can see the user has got his Voice Mail option available.
Hope this was useful
—-
UM gateway

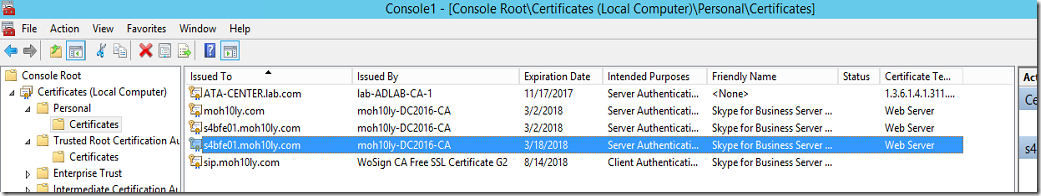

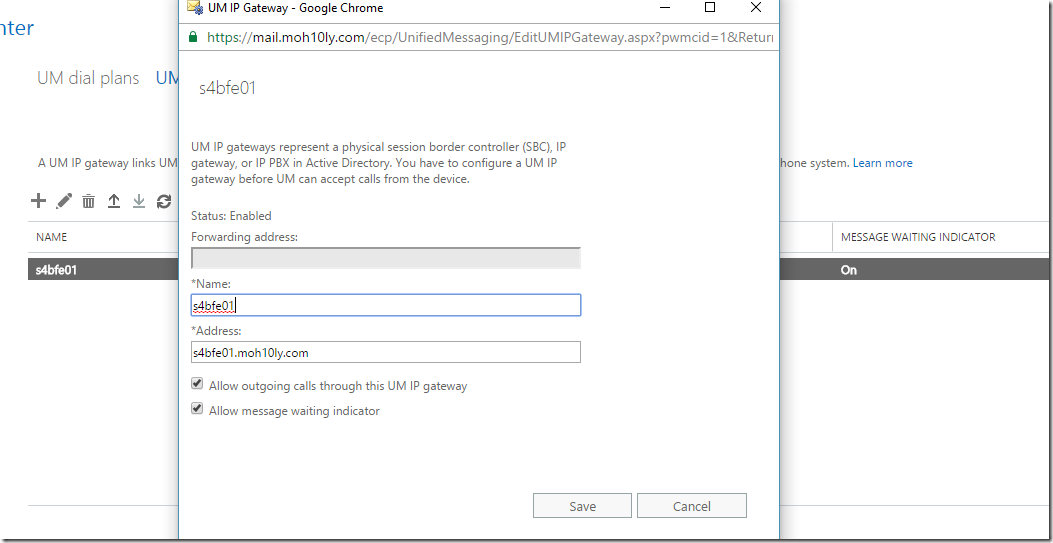
I have 5 SfB FE, the certificate created in SfB imported in Exchange, I have to install that same in the other FE’s, because that only includes the name of that FE in the SAN’s
Thank you.
Hi Ray,
True, In order for UM to work the certificated generated on all Frontends must have all of Exchange and Frontend servers FQDN included in order for the UM to flow properly in all servers.
This is a very healthy method of trusting traffic between Exchange servers and Frontends.
You can basically generate a single certificate that include all your Frontend servers and all your Exchange Servers, Export this certificate with the key and import it on all other servers and on Exchange assign it to the UM services. That should do the trick.